HUB Security Adds Docker Security to Encryption Platform
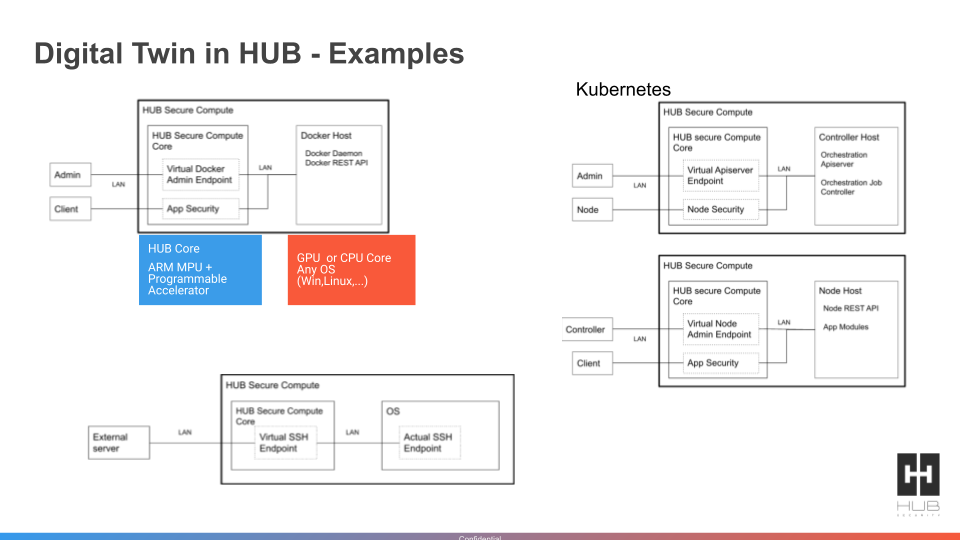
HUB Security has added a Docker Digital Twin platform that secures, authenticates and verifies traffic created by Docker containers running on an encrypted hardware platform.
Noam Dror, vice president for worldwide solution engineering at HUB Security, says as Docker containers are more widely used across enterprise IT environments, it’s clear that cybercriminals are specifically looking to exploit multiple container vulnerabilities discovered using scanning tools.
The HUB Security Docker Digital Twin platform enforces access control, such as approvals for sensitive actions on incoming Docker traffic, to block attack vectors involving the loss or theft of credentials, unauthorized access or attempts to exploit known Docker vulnerabilities, Dror says.
HUB Security has developed an encrypted computing platform aimed at preventing hostile intrusions at the hardware level in addition to offerings that prevent the theft of data. The Docker Digital Twin platform will be incorporated into existing HUB Security technology without changing existing operational controls and services. It is designed to be compatible with all versions of Docker.
Most recently, HUB Security revealed it is partnering with QuantLR, a quantum technology research company, to build a quantum security solution for the Israeli Ministry of Defense. The solution will protect sensitive information in cloud environments. That platform includes user identification capabilities as well as encrypts documents, presentations and spreadsheets through encryption keys generated by a quantum computer.
Container security has become a major concern of late. Most of the applications organizations are deploying to drive digital business transformation initiatives are being built using containers. Given the mission-critical nature of those applications, they are increasingly being targeted by cybercriminals. The challenge organizations face is that the developers building those container-based applications don’t have a lot of cybersecurity expertise. HUB Security is making a case for securing those applications at the hardware level to prevent unauthorized interactions without relying solely on developers to secure them.
Historically, the biggest container security threat has involved cryptojacking—illicit cryptocurrency mining—which is generally considered a nuisance crime. However, it’s also clear that cybercriminals have found more severe ways to compromise containers. It’s only a matter of time before more serious attacks are launched using the same attack vectors employed to mine cryptocurrencies. Most of those attacks involve compromising the developer’s credentials.
It’s not clear whether container security concerns might prompt an organization to invest in encrypted hardware platforms to secure their applications. However, as more enterprise-class applications are built and deployed using containers, there will undoubtedly be more organizations looking to encrypt those applications.
In the meantime, IT organizations should not assume containers are more secure than any other software artifact. After all, it’s not the containers themselves that are the issue—it’s the vulnerabilities of the software components packaged in those containers that are the real cause for concern.