Sweet Security Unfurls Cloud-Native Runtime Protection Platform
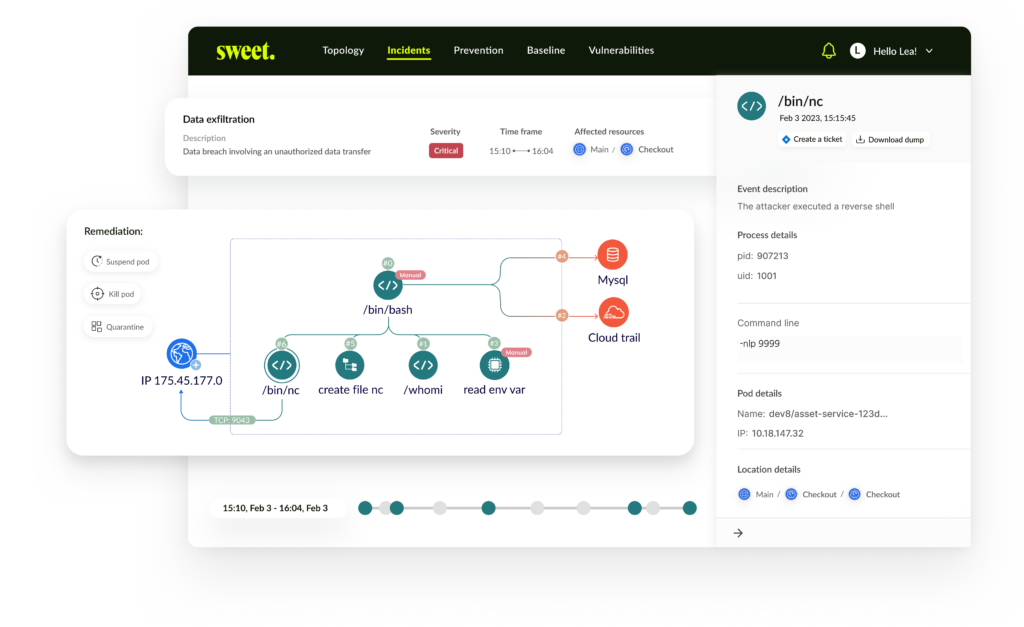
Sweet Security today launched a Cloud Runtime Security Suite platform for securing cloud-native application runtimes. The platform uses a sensor that streams application data to its servers that runs a framework to profile workload behavior anomalies.
Fresh from raising $12 million in funding, Sweet Security CEO Dror Kashti said existing threat detection tools provide limited functionality or aren’t optimized for cloud-native environments.
The Sweet Security sensor provides insights into attacks both before they are launched and as they occur, said Kashti.
Designed to be deployed in less than five minutes, the sensor feeds data back to an attack detection model Sweet Security has developed for cloud-native application runtime environments. Those models provide application security teams with the context required to effectively respond to the threats based on the actual runtime topology, noted Kashti.
That approach also streamlines the large volume of alerts that would otherwise be generated across cloud-native application environments that are made up of multiple microservices.
At a time when more applications than ever are constructed using containers to create microservices, securing applications has become more challenging. Despite those challenges, however, organizations are also being held more accountable for securing their applications both as they are built and after they are deployed. Various laws and regulations will require organizations to demonstrate they’re making a good-faith effort to secure their applications whenever there has been a breach.
Historically, too many organizations allowed developers to aggregate software components without always checking to see if they were compromised. Many of the same vulnerabilities that impact legacy applications still exist in a cloud-native application environment. The only difference is they are encapsulated in a container that may only run for a few seconds. When there are thousands of containers running, however, it doesn’t take much for cybercriminals to exploit them.
Cybercriminals are also becoming increasingly adept at injecting malware into software components in the hope that it will find its way into downstream cloud-native application environments. In fact, it’s been demonstrated that malware can “jailbreak” from a container to give cybercriminals access to the entire runtime environment that multiple applications share.
It’s not clear how much focus there is on securing cloud-native application environments, but as more mission-critical applications are built and deployed on Kubernetes clusters, it’s only a matter of time before cybercriminals look for ways to compromise the software supply chain relied on to build and deploy them. Fortunately, more organizations are also embracing DevSecOps best practices to better secure those supply chains.
In the meantime, however, there’s a considerable number of cloud-native applications that have already been deployed. The level of technical debt that needs to be addressed only increases with each application deployed. In an ideal world, those vulnerabilities would be addressed before an application is ever deployed. In practice, however, the applications’ runtime is the last line of defense.