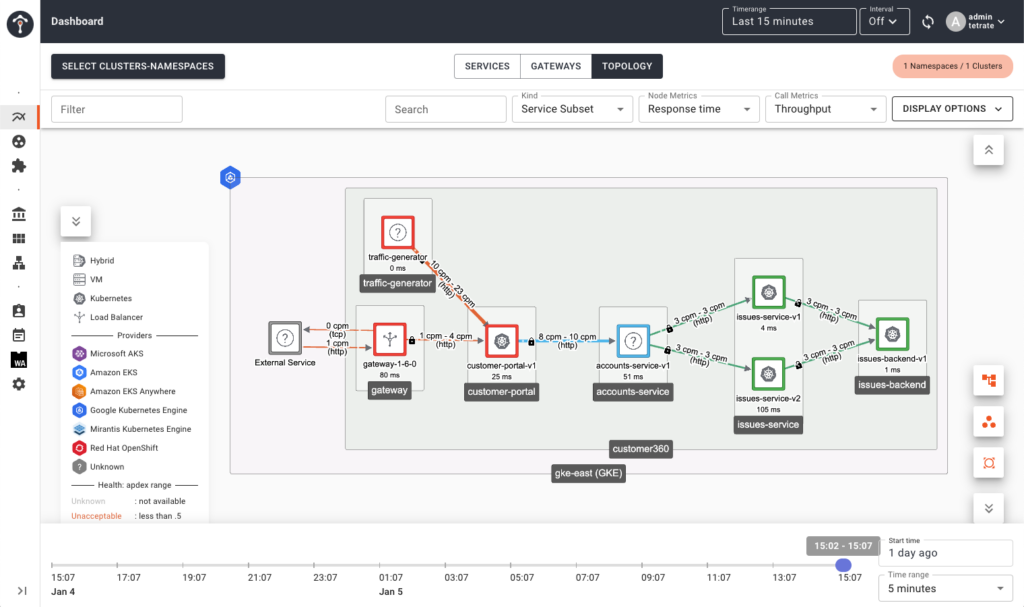
Tetrate’s Brooklyn update to its distribution of the open source Istio service mesh automates deployment of security policies.
In addition, high availability has now been extended across clusters, regions and clouds running the Tetrate Service Bridge (TSB) with no manual intervention required.
Finally, the company is making available a set of best practices for deploying TSB and has hardened the platform for use in production environments.
Tetrate CEO Varun Talwar says that while TSB provides IT teams with a service mesh that can be deployed on Kubernetes clusters, the company has gone a step further by integrating legacy platforms with its service mesh. As IT environments become more complex in the cloud-native era, Talwar says it’s apparent there is a need for a service mesh that spans multiple platforms.
That approach will enable IT teams to programmatically manage security and networking at a high level of abstraction, he says. The goal is to provide these capabilities in a way that makes it simpler for developers to self-service their requirements in a way that can still be centrally managed, notes Talwar.
Most organizations initially adopt a service mesh to manage application programming interfaces (APIs) across a cluster. As organizations deploy fleets of Kubernetes clusters, the need to centrally manage APIs becomes more acute in a cloud-native application environment. Organizations are increasingly adopting Istio as the control plane, Envoy as the data plane, the Kubernetes Gateway API for ingress and BoringCrypto for FIPS 140-2 approved cryptographic algorithms to achieve that goal, says Talwar.
However, organizations also have legacy monolithic applications that will not be replaced any time soon; the need to manage services at a higher level creates a need to extend Istio, he notes. The extensions make it possible, for example, to enforce security policies in alignment with corporate policies while also allowing for exceptions involving unique application use cases, says Talwar.
It’s still early days as far as adoption of service mesh platforms in production environments is concerned, but the way networking and security services are managed is on the cusp of major change. Instead of waiting for networking and security operations teams to provision services, each development team will be able to self-service their own requirements within a set of guidelines defined by a central IT management team. That approach will also make it much simpler to integrate the provisioning of those services within DevOps workflows to accelerate application deployment.
There is, of course, no shortage of options when it comes to service mesh platforms, and it will undoubtedly take time for the culture within IT organizations to evolve as more instances of service mesh platforms are deployed. In the meantime, IT teams would be well advised to, at the very least, start aggressively experimenting with service meshes—if for no other reason than to provide a layer of abstraction for managing everything from APIs to underlying networking services and eliminate a lot of the low-level tasks that get in the way of building and deploying software.